After a career in police investigations based out of London, Shaun moved to Trondheim where he now works as a consultant with Transcendent Group, advising in the areas of Information Security, Quality Management Systems, Investigations, Business Intelligence, Risk and Business Continuity.
In this article, I will examine more closely what we mean by intelligence and how that differs from information. I will also address how to deal with the information acquired. It should be noted that in this article I am addressing issues generically and when considering action to be taken it must, of course, be tested against the legality of what is permissible in the jurisdiction in which you are operating.
Part of identifying and assessing risk must surely be to anticipate what the opposition have access to and what their capabilities are. If it works for them it can work for you, so a systematic approach to gathering information and turning it into intelligence is needed. It doesn’t have to be the stuff of fiction or Hollywood films; this is not the Bourne Trilogy and you don’t have to look like Matt Damon.
There are many companies that provide intelligence gathering services for their clients. Brand protection is but one reason for this. A lot of the intelligence gathering takes place on the internet and you would be truly surprised at what can be found. There are many books written on the subject of Open Source Intelligence (OSINT) and there are hundreds, if not thousands of free tools available on the internet to gather and mine this information. Some nation states employ tens of thousands of people to gather and exploit information. Countries such as Norway have a reputation for technology and innovation, so they especially present themselves as an attractive target.
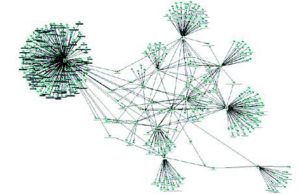
As a penetration tester, I spend a lot of time gathering information before even attempting to test a system. Figure 1 shows the result of OSINT gathering and then visualizing it to aid understanding. Each node is information freely obtained and shows the links between people, companies, hobbies etc. Put together this information can either make you stronger or destroy your business.
So, everyone knows what information is! It’s anything you can sense, see, touch or hear. It can be rumours, speculation or even the truth.
Intelligence, on the other hand, is something more, well, intelligent. It is the collection and receipt of information, assessing it for reliability and provenance, identifying gaps, obtaining and analysing the additional information. Just because it is on the internet or in the papers doesn’t make it true. Besides, what is important to one organization may not be important to yours. The result is something that informs your business processes.
Let’s now step through the first stages that can be adopted to make you more ‘intelligent’.
Consider how many sources of information you have access to. The list is endless. Now consider what could give you a warning that something untoward is about to happen to your business. Then ask yourself why someone would want to do this? It could be that you have just launched a new product which ‘flattens the competition’.
It could be that your product or service will ‘provoke’ special interest groups or your Research and Development process is enviously regarded. So firstly, ask the question ‘Where will they get information?’ In other words, ‘Espionage’. Your web site seems a good place to start.
Putting aside such illegal methods as blackmail, kidnapping, burglary and theft, consider what information is openly held, where it is and how they could access it. The first point of their intelligence gathering could be your internet presence.
You hopefully have decent logging enabled, not to mention protection from attacks. Does the coding in your web page reveal sensitive information? You would be surprised what people write when they think it can’t be seen. I have seen ‘secret’ email addresses as well as comments that refer to the location of sensitive data.
In one case, an international group of paedophiles used virtually untraceable email addresses to communicate. They then used several other internet tools to split the information up. However, just leaving information in the web page circumvented their security and resulted in some pretty lengthy stays as a guest of the state.
People gathering information will, in all probability, have left traces on the internet during previous activities. This can help you build an assessment of their motivation and capabilities. Having a structured way to gather this information, and turn it into intelligence, seems like a good idea. Better to know that someone is looking than get surprised.
Consider cause and effect. Again, risk identification and planning are essential. As the old saying goes: It’s too late to learn to dance five minutes before the party.
Time now to apply some thought. The first thing to assess is the source of the information. This could be graded as follows:
You could assign a value to these assessments either by a letter or a number. Either way, be sure to evaluate each piece of information on its own.
The second step is to evaluate how the source knows this information? Again, the criteria could be:
A third step may be desirable and is used for determining who or where the intelligence should be disseminated to. It could be that the source or the information is ‘business sensitive’ and it should be protected. This is a matter for you, but again a grading system could be adopted.
You are an organisation who produces a successful range of designer furniture. You have had some protests from environmental groups in the past due to the use of hardwood from non-sustainable forestry sources. The protests previously have been nonviolent and involved the use of social media and letters to some of your retailers. However, a threat was made that should this continue then ‘other action’ may be taken. You are just about to launch a new line of furniture and will announce it on your website.
This example is used to illustrate the potential sources of information to be collected and evaluated during your risk assessment.
Above all, have a systematic plan to collect, record and evaluate and deal with the consequences. Make sure all interested parties have access to it, and if possible, exercise your plan so everyone knows what their role is.
By now you should be well on the way to appreciating the information you already have access to, be aware of the additional sources of information available and understand the importance of applying a defined and structured method of evaluation to this data.
Realising that this intelligence may come in dribs and drabs, a method of storing and collating data is needed, and this is where the thorny question of data protection law comes in to play. I can only encourage you to comply with your own country’s laws and regulations. Compliance is always a risk element to be considered and mitigated given its potential to damage your organisation’s bank balance and reputation.
The system should be capable of being searched for words and ideally utilize basic search logic such as AND or OR statements. Each piece of information should have the source and evaluation criteria attached. At the very least, a spreadsheet will suffice. This can be incorporated into your overall risk planning although it is very dynamic by nature. Remember you can´t avoid an investigation but you can at least think about it and plan for that eventuality. For those of you that remain to be convinced consider the GDPR regulations that came into effect in May 2018. Many companies are NOT ready and I would predict that there will be several investigations by the regulators into breaches of information security, some of which could have been prevented by defined intelligence gathering procedures.
Once you have overcome this potential barrier you can proceed to the next stage which is analysis. This function comes in several different flavors ranging from simple to that requiring a PhD. For our purposes, we’ll use the KISS principle (Keep It Simple, Stupid).
In the context of this article this means ‘What do we know now, and what would we like to know in the future?’ The bit in between is the gap that needs filling. The gap can be to find out more about a competitor’s product, to determine why your share prices are changing unexpectedly or to understand the capability and intent of people opposed to your product, as mentioned in the first part of this article.
The result of this analysis could drive another round of collection, evaluation and collation, but this time with a specific task in mind. You are intelligently tasking, and that is more efficient in terms of time and resources.
Once you have sufficient data, you can proceed to other more complex types of analysis. This can be timelines, cause and effect studies, business modelling etc. The type will depend on your needs and abilities. It is at the analysis stage that the mists should start to clear, and a clearer picture of the situation emerge.
One of the quirks of analysis is that you will rarely get all the answers written in stone. Some things you will know as facts, and others you will have to infer. The evaluation methods shown in this article will certainly help in this respect, as you will have a set of criteria to assess the information against. Inferences are useful when formulating working theories.
I mentioned above that tasking is an important part of the intelligence process. Tasking (and the reasons) should be recorded and this applies whether you yourself perform the task, or you assign it to someone else. In fact, any decision taken should be recorded with as full a rationale as possible.
If you are subject to an investigation, they will want to know why certain actions were taken. Having a contemporaneous record of a decision, whether right or wrong, is better than “I can’t remember” or worse; making your answer fit the circumstances in hindsight.
Some people run dedicated written ‘decision logs’ covering a range of topics such as media, communications etc. However, as long as it’s recorded somewhere, can’t be altered and is available, then any medium will suffice. It will help to answer those horrible questions such as ‘when did you know’ and ‘why did you do that’.
In my experience, the post incident review often involves much finger pointing, people running for the bushes and putting extra clothing on that part of the body that we sit on!
So, you’ve put all this effort in, you’ve identified risk or threat, you have collected, evaluated, collated, analysed, tasked and analysed again. Now it’s decision time:
This is where all efforts can come to naught because the information is not disseminated or shared to those who need it.
So, what should the output be from all this work? If everyone has the ability to feed information in should they also have the right to see the resulting intelligence? Not surprisingly the answer to that question is an emphatic no.
One principle that should always be adopted is the ’need to know principle’. There is some information which should not be freely available because once information is released, it is impossible to know how far it has gone, who now has it, and what they will do with it.
Research suggests that the biggest threat to corporate or organizational security comes from within, and this includes espionage. If you have ever ‘misplaced’ sensitive data, then your priority will surely be to conduct ‘propagation analysis’. A potentially costly and sleep depriving exercise, which I will illustrate by describing a case I worked on involving the loss of sensitive data.
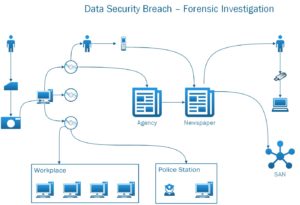
Figure 2 shows the result of a very fast time computer forensic investigation to determine whether the data contained in the SD card shown on the left had been copied and, if so, who else had access to it. Apart from the sensitivity of the data I would suggest that the primary objective was to determine the degree of propagation and assess the risk to the data subjects. By following the forensic clues coupled with good old detective work´ I managed to trace the data flow, identify who had seen it and ring fence it within 36 hours. My confidence level was high that the information was safe, but had it gone any further the outlook would have been quite pessimistic. The point here is “Need to Know”.
During your intelligence process you may have adopted a grading system for each piece of information relating to its dissemination. Even if you have not done this, then you should consider whether the final report should be protectively marked with something like ‘Commercial – Sensitive’ and restrict its circulation. If this report forms part of your general contingency planning, then extracts or a summary can be made freely available. You can also store the report within your crisis management system and restrict access by role or a named individual. Again, assess the risk of disclosure and any possible impact.
This article has focused on the need for a systematic approach to gathering information, assessing it and turning it into actionable intelligence. The techniques described, albeit briefly, are tried, tested and battle-proven across a whole range of activities from intelligence agencies to the largest corporations. Business intelligence (BI) is intelligent business. BI drives many functions from client selection, acceptance and product development, to risk, contingency and crisis management.
Written by Shaun Reardon
First published in IIA Norway’s magazine SIRK 2018/1